centos change ssh port
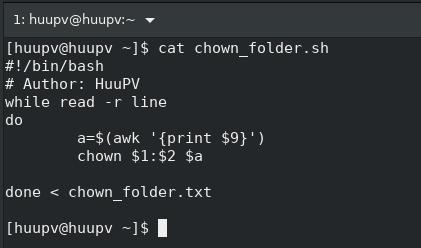
in this tutorial, How to change ssh port another with selinux. The default ssh port 22, when you change port another with rules selinux (SELINUX=enforcing) get error can't change ssh port. Solve problem!( Running command following with root account) File selinux with content SELINUX=enforcing as below: [huupv@huupv ~]$ sudo cat /etc/sysconfig/selinux [sudo] password for huupv: # This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - No SELinux policy is loaded. SELINUX=enforcing # SELINUXTYPE= can take one of these three values: # targeted - Targeted processes are protected, # minimum - Modification of targeted policy. Only selected processes are protected. # mls...